Cyber threats create many news headlines, with a massive number of data breaches at the important organization and computing systems of government agencies being shut down for ransom. However, Cyber threat is not just a significant problem for a larger organization and national governments. Cybercriminals target individuals as oppressively constant as they go after large companies and national government. The average user is on their own when it comes to his personal computers and devices security, while a chief executive of companies can afford a dedicated and specialized cybersecurity team. Due to this, millions of potential targets exposed to the risk of being attacked, it can range from the sort of data theft and ransomware which is commonly used to target national government agencies, personal computer, an organization to create more personal attacks that aim to cause chaos and distress.
Cyber Crime is expected to exceed $2 Trillion annually by 2019. Morgan, S. (2016, January 17). Forbes
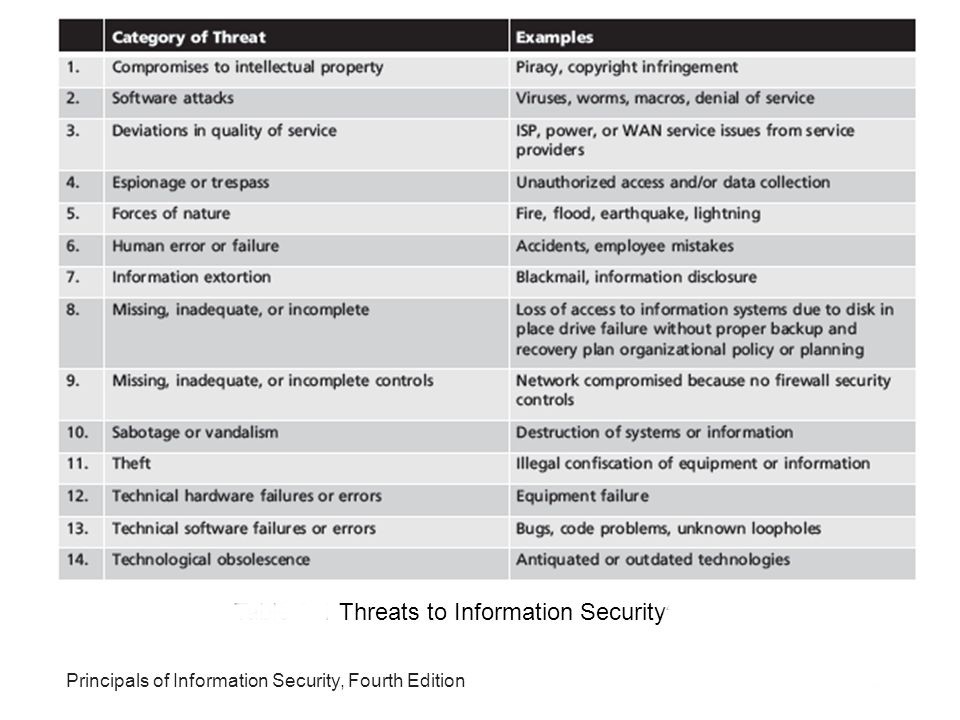
Compromises to Intellectual Property
Intellectual property is one of the most dangerous and damaging ways; an insider can put the organization at risk by stealing their ideas, inventions, and creative expressions. An organization cannot ignore the value of its trade secrets and proprietary products and parts to movies, music, and software and customer information lists. An insider has various reasons to commits these crimes such as to gain a competitive business advantage, for the benefits of another entity, for the personal financial gain, or to start a competing organization. IP is growing threat nowadays especially with the rise of digital technologies and internet file sharing network. This theft costs U.S. businesses billions of dollars a year and robs the nation of tax revenues and jobs.
Software Attacks
Software Attacks is an attack which can run an executable file in order to load a trojan, worm, virus or other harmful malware on the system. Interesting facts is this that most of the user think that ARP spoofing, cache poisoning, cross-site scripting, data security, keylogger, LDAP injection, computer malware, virus, sniffing, trojan, spyware, and botnet are all the same. However, they are not the same; the only similarity is that they all are malicious software and scripts which behave differently.
Deviations in Quality of Service
Deviations in service quality can cause by many issues to occur, and most of the time, it has nothing to do with information technology. For a railway station to function appropriately, electricity, internet, and telephone are necessities. An interruption to these necessities could cause a significant incident and disrupt the workflow.
Espionage or trespass
In Railway Stations, eavesdropping and hacks are the biggest threats to network security. These types of attacks can be done quietly effortlessly and with minimal risk of detection. Cybercriminals use espionage to accomplish their tasks. Cyber terrorists can attack anywhere where the physical and the virtual worlds combine. The Internet and computer technology have made possible these attacks. Attackers do not have to be anywhere near the city, state, or country in which the attack is being executed, which makes it worst. Due to the high level of the software being deployed by the railway station, the hackers usually have to obtain mastery level skills in order to get into the system. That mastery level of skills includes possession of knowledge of multiple programming languages, networking protocols, and operating systems.
Forces of Nature
Forces of mother nature are among the most dangerous threats. It not only disrupts individual lives, but also can destroy the storage, transmission, and all kind of use of information. To deal with Fire, flood, earthquake, and lightning, An Organizations, must implement such controls to mitigate damage and create a backup to keep continued operations.
Human Error or Failure
Employees are always a threat to their organization. An employee’s mistake can be very harmful to the organization’s classified data. Even misleading data and data deletion by accident or any medication with data lead to a significant threat to the organization.
Information Extortion
An attacker use networks to execute different sorts of threat including extortion. Various forms of extortion are requested on the front-end and others on the back-end. An attacker uses their skill to make a name for themselves, as a means of gaining wealth from others involuntarily, or as form blackmail to keep from disclosing the information. Cybercriminals are using this threat as part of an ‘extortion racket’ with money being demanded to prevent the launch of such an attack.
Missing, Inadequate, or Incomplete
Where we discussed the loss of access to information systems, due to disk drive failure without proper backup and with no proper recovery plan, or organizational policy or planning.
Missing, Inadequate, or incomplete controls
If we do not install firewall security control into our organization’s network systems and it can compromise anyone.
Sabotage or Vandalism
Due to recent attacks in a different organization, the railway industry has invested countless resources building greater checks and balances into its security processes. However, attackers and vandals continue to seek out means of exploiting security loopholes. These threats can manifest from almost anywhere, such significant corporations like railway must be prepared.
Theft
Acts of theft are an illegal taking of another’s physical, electronic, documents, devices, or any shape and kind of intellectual property. They can easily control physical theft as a comparison to electronic theft, which has a more complex sort of problem, in this case, evidence of a crime not readily apparent.
Technical Hardware Failures or Errors
Technical hardware failures are one of the significant risk factors in an organization. It is one of commonly talked-about reason to perform backups. Experts can realize the importance of backup when this end with an unrecoverable hard disk failure. We also know that the hard disk stores data and primary programs. In this case, it is the hardware whose failure hurts the most. If we talk about others hardware problems, then memory errors, system timing problems, resource conflicts, and power loss are those whom can cause permanent data loss.
Technical Software Failures or Errors
The importance of software functionality in an organization is very much crucial for the availability, integrity, and authenticity of data. If they are facing any hard work, awkward, confusing process while accessing data, then this could be possible due to software functionality errors, bugs, syntactic error or maybe at handling process phase. We have to make sure about all there systems software updated with the latest bugs fixed patches.
Technological Obsolescence
Any kind of outdated technologies in both way, hardware or software could be dangerous and risky for data process and security.
Cyber Attacks and its Impacts
The Morris Worm
It was one of the first recognized worms to affects the world’s nascent cyberinfrastructure. It widely spread around computers in the US. The primary worm purpose of analyzing and examine the weaknesses in the UNIX system Noun 1 and replicated itself regularly. Its primary function was to slow down the computer to the point of being unstable. Robert Tapan Morris developed it. His confessional statement was a bit interested as he said, he was trying to gauge how big the internet was.
It was the first Distributed Denial of Service (DDoS) attack, and it was entirely by accident.
In total, the worm damaged approximately 6,000 computers. The estimated cost of repairing the effects of the worm range between $100,000 and $1 million or between $201,000 and $2.9 million adjusted for inflation. Morris was charged with the violation of the Computer Fraud and Abuse Act, and his sentence included fines, plus three years of probation and community service. (Climer, 2018)
whistler
Josef Carl Engressia, Jr. is born May 25, 1940, in Richmond, Virginia, USA, he born blind and was an early phone phreak. Born blind, at the age of 5, Engressia discovered he could dial phone numbers by clicking the hang-up switch rapidly, and at the age of 7, he discovered that whistling at certain frequencies could activate phone switches.
He had absolute pitch and was able to whistle 2600 hertz into a telephone; He was given the nickname “Whistler” in late 1960 by the University of South Florida’s student. He can easily place free long-distance phone calls by using the whistle method by creating proper tones with his mouth. He was suspended from the university and was fined 25 $ due to Report from Canadian Operator for selling $1 call at the university.
Kevin Mitnick
Kevin Mitnick at age 12, used social engineering. He successfully convinced a bus driver to tell him, where he could buy his ticket punch, with good transfer slips, he was able to ride any bus in the greater LA area and found Transfer slips in a dumpster next to the bus company garage. Later he starts taking an interest in social engineering for obtaining information, including usernames and passwords and modem phone numbers.
In 1979, Mitnick first gained unauthorized access to a computer network. One of his friends gave him the phone number for the Ark to break, the computer system Digital Equipment Corporation (DEC). They used DEC for developing their RSTS/E operating system. Mitnick successfully broke into DEC’s computer network and copied their software, a crime for which he was charged and convicted in 1988. In the beginning, DEC reported damage was $ 4 million but later during hearing they disclose it was actual $1,60,000. (Delio, 2002)
The Purloined Password
The security breach at NCSS triggered at that time, and it was investigated by The Federal Bureau Investigation (FBI). This incident reported by The New York Times in 1981. New York Times describes white hat activities as part of a “mischievous but perversely positive ‘hacker’ tradition. One of NCSS Employees creates Password crackers to use on the customer account. No significant cash or data loss has yet been associated with the theft, but with its ominous possibilities, the NCSS security scandal has badly jarred the vast $8 billion-a-year remote processing industry. (Mclellan, 1981)
The Captain Zap
Ian Murphy, known to his friends as Captain Zap, was the first cracker to be tried and convicted as a felon. Murphy broke into AT&T’s computers in 1981 and changed the internal clocks that metered billing rates. People were getting late-night discount rates when they called at midday. Of course, the bargain-seekers who waited until midnight to call long distance were hit with high bills. (Delio, 2001)
The 414s
It was the group of 6 peoples aged between 16 to 22 years old. They broke into the system, who were exclusively running Digital Equipment Corporation’s (DEC’s) VMS and RSTS operating systems at institutions ranging from, Los Alamos National Laboratory to Manhattan’s Memorial Sloan-Kettering Cancer Center. They used various inexpensive personal computers, analog routers, and simple and complex hacking techniques, such as using common or default passwords published in DEC’s manufacturer guides to log in to various timeshare systems. The 414s exploited a lack of administrative oversight and password care for systems.
The 414s were investigated and identified by the FBI in 1983. There was widespread media coverage of them at the time, and on September 5, 1983, it was the cover story of Newsweek with the title “Beware: Hackers at play.” They gave nearly $1,500 worth of damage at Sloan-Kettering during their June 3, 1983 break-in by deleting billing records.
The MOD and LOD Squads
In 1993, the Masters of Deception (MOD) was the first crackers ever to get busted via wiretaps. They were famous for finding the ways to avoid paying for long-distance calls and could also sneak in on private conversations, and create strong party lines that allowed many people to chat to each other at one time. MOD also find a way into many a database, including those belonging to the NSA, AT&T, and the Bank of America. They also accessed that time credit-record reporting agency TRW’s computer system and successfully able to gain access to rich’s people credit report.
MOD was also got fame for the wars they started in with the Legion of Doom (LOD), another powerful cracker group that had the reputation of being the headquarters for the most elite hackers. Due to internal struggles among the members, the infamous cracker Phiber Optik left LOD and formed MOD. The groups then battled each other for the crown of Cracker King for years, until most of them got busted in 1993. Many say that MOD members would not have gotten caught if they had not been competing against LOD; so many experts said if the war made them less cautious than they should have been. (Delio, 2001)
Kevin Mitnick
Snagged by the FBI on Feb. 15, 1995, Kevin Mitnick was the very first person to be convicted of gaining access to an internal computer network for criminal purposes. He was also the first cracker to have his face appear on an FBI “Most Wanted” poster. Mitnick was charged with, stealing at least $1 million worth of sensitive project data from computer systems,snagging thousands of credit card numbers from online databases, breaking into the California motor vehicles database, and remotely controlling New York and California’s telephone switching hubs on various occasions – moreover, he also possessed the uncanny ability to convince home phones that they were really paid phones.
He has, however, denied cracking the NORAD (North American Air Defense) Command computer, a crack that was widely credited to him and inspired the movie War Games.
Mitnick was also a champ at what hackers refer to as social engineering, gathering information just by asking people for it. Many times, the passwords he used to enter computer networks were provided by the systems administrators of those networks, who had been convinced that Mitnick had good reasons for needing the passwords. (Delio, 2001)
Citibank Heist
The year 1995 also marked the great Citibank heist, when Vladimir Levin, a graduate of St. Petersburg Tekhnologichesky University, convinced Citibank’s computers to transfer $10 million from its customers’ accounts to bank accounts around the world. Vladimir Levin, the 30-year-old ringleader, uses his work laptop after hours to transfer the funds to accounts in Finland and Israel. Interpol caught up with him at Heathrow Airport. Authorities recover all but $400,000 of the stolen money. Levin stands trial in the United States and is sentenced to three years in prison. (“List of notable security hacking incidents,” n.d.).
LA KIIS FM Porsche
A computer hacker who rigged telephone lines to win contests sponsored by Los Angeles radio stations KIIS-FM, KPWR-FM and KRTH-FM. Kevin Lee Poulsen, 29, of North Hollywood, pleaded guilty in 1995, to using computers to rig telephones at the three radio stations so that he and his accomplices would be the winning callers. During a two-year period that began in 1989, Poulsen and the others won two Porsches, at least $22,000 in cash and two trips to Hawaii.
In giving the hacker–known as “Dark Dante”–the longest sentence ever handed down for such a computer crime, U.S. District Judge Manuel Real ordered Poulsen to pay restitution of $36,925 to KIIS, $20,000 to KPWR and $1,000 to KRTH. Poulsen had initially been faced a term of 30 to 37 months in prison, but Real added time because the defendant could have jeopardized federal agents when he broke into a Pacific Bell computer in August 1989, to get information about FBI wiretaps. (Los Angeles Times, 1995).
Defense Department computer
In 1996, The U.S. General Accounting Office reports that hackers attempted to break into Defense Department computer files some 250,000 times in 1995 alone. About 65 percent of the attempts were successful, according to the report. (“List of security hacking incidents,” n.d.).
DOD Computer Penetrations
The U.S. Naval Academy computer system was successfully penetrated in December 1994. Sniffer programs were installed on servers, the system’s name and address were changed (making the system inaccessible to authorized users), files were deleted, password files were compromised, and more than 12,000 passwords were changed (U.S. General Accounting Office, 1996).
In March 1997, a computing system at Anderson Air Force Base in Guam was penetrated by a 15year-old working from Croatia and using programs freely available on the Internet (Computer Penetrations,1997).
During the Gulf War, e-mail and information about troop movements and missile capabilities were stolen from DOD computers by hackers based in Eindhoven, The Netherlands. The information was then offered for sale to the Iraqis, who rejected the offer, thinking it a hoax (Schultz, 1997).
As part of a June 1997 exercise (“Eligible Receiver”), an NSA hacker team broke into the U.S. electric power grid system and DOD They simulated 911 emergency telephone overloads in Washington, D.C and a series of rolling power outages, and other cities. They also succeeded in breaking into unclassified systems at four regional military commands and the National Military Command Center in Washington. Moreover, they gained supervisory-level access to 36 networks, enabling e-mail and telephone service disruptions (Gertz and Myers, 1998).
In October 1997, the U.S. State Department shut down portions of one of its international computer systems after the General Accounting Office discovered evidence of an intruder in computers at two overseas posts. The affected computer system links computers in Washington with 250 U.S. embassies and consulates (Zuckerman, 1996).
Microsoft’s Windows NT operating system
The hackers are taking advantage of a bug in Windows NT 4.0 running Microsoft’s Internet Information Server 3.0, in which the entire site jammed by someone typing in a specific URL into a Web browser, according to Mike Nash, director of marketing for Windows NT server. (Hackers jam Microsoft, 1997)
Pentagon Deflects Web Assault
An online political performance-art group”Electronic Disturbance Theater”, attacks the various high-profile websites, including the website of Mexican President, Pentagon, Stock Exchange, and the Frankfurt Stock Exchange by asking demonstrators to load a hostile Web-based program called FloodNet. Electronic Disturbance Theater called it conceptual art and claiming it to be a protest, the method of suppression of the Zapatista Army of National Liberation in southern Mexico. EDT uses the FloodNet software to bombard its opponents with access requests. (Mckay, 1998)
Hackers Leave Ransom Note on Yahoo Site
Hackers broke into Yahoo, the Internet’s most popular site, demanding the release of an imprisoned comrade Kevin Mitnick and threatening to unleash a crippling computer virus if he is not freed. Computer security experts, however, were skeptical of the hackers’ claim that they had implanted such a virus. (“Lancaster,” 1997)
Cameron LaCroix, aka camo
An American computer hacker knew for the hacking of Paris Hilton’s cellular phone. The teen also pleaded guilty to making bomb threats at two high schools and for breaking into a telephone company’s computer system to set up free wireless-phone accounts for friends. He also participated in an attack on data-collection firm LexisNexis Group that exposed personal records of more than 300,000 consumers. Prosecutors said victims of the teen’s actions had suffered about $1 million in damages. He has also been convicted federally of identity fraud, System fraud, wire fraud, and making a false bomb threat. Prosecutors said victims of the teen’s actions had suffered about $1 million in damages. Under a plea agreement signed by the juvenile in August 2005, he received 11 months in a federal juvenile detention facility. In January 2007 his supervised release was revoked for a string of similar crimes and possession of a cell phone and another computer-related equipment. (Krebs, 2005)
No site is safe
Xiao Chen and around 19 other Chinese hackers claim back in 2008 to have gained access to the world’s most sensitive sites, including The Pentagon. Private computer experts in the United States from iDefense Security Intelligence, which provides cybersecurity advice to governments and Fortune 500 companies, say the group’s site “appears to be an important site in the broader Chinese hacking community.” They operated from an apartment on a Chinese Island. (Vause, 2008)
Trend Micro
Trend Micro confirmed that several of Trend Micro’s Web pages had been hacked, the security vendor’s infected Web pages were part of a massive attack affecting more than 10,000 Web sites. Attackers infected the otherwise trusted Web pages with password stealing loggers, backdoors and other types of malware on the PCs of users visiting the sites. (Hoffman, 2008).
Bank of America
Bank of America website got hacked by a Turkish hacker named “JeOPaRDY.” An estimated 85,000 credit card numbers and $100,000 were reported to have been stolen due to the hack. Bank officials say no personal customer bank information is available on that web-page. (Kumar, 2011)
PlayStation data breach
An “external intrusion” sends the PlayStation Network offline, and compromises personally identifying information (Names, birthdates and some credit card data) of its 77 million, estimated losses of $171 million while the site was down for a month., including more than one million in Canada, are registered with the network that suffered a massive data breach. More than 70 percent of PlayStation 3 video game consoles are connected to the PlayStation Network, which allows users to play online games, surf the web, chat with friends and download games and other content from the PlayStation Store. In 2014, Sony agreed to a preliminary $15 million settlement in a class action lawsuit over the breach.
The breach also affects users of Sony’s Qriocity service, which streams movies on demand to compatible Sony devices such as HDTVs and Blu-ray players for a monthly fee. The company said it could not provide user statistics for Qriocity. (Chung, 2011)
Federal worker pay stub
A mysterious security breach has led the federal government to shut down its online payment system, affecting some 320,000 public servants. Several reports based on unidentified sources claimed China was the source of the attacks, attack. The system was pulled offline for “urgent” repairs on April 4, 2011. After officials discovered the privacy of eight account-holders had been breached. Electronic paystubs with information about basic salary, overtime, bonuses, reimbursement of travel expenses and other vital data have been unavailable for more than two weeks. The glitch affects virtually every federal department, from Health Canada to Public Works itself, which operates the self-serve online system for all government employees. The affected system, known as the Compensation Web Application or CWA, was set up in 2005 and has never been offline for so long. (Breach halts electronic, 2011)
Yahoo
In September 2016, the once-dominant Internet giant, while in negotiations to sell itself to Verizon, announced it had been the victim of the most significant data breach in history, likely by “a state-sponsored actor,” in 2014. The attack compromised the real names, email addresses, dates of birth and telephone numbers of 500 million users. The company said the “vast majority” of the passwords involved had been hashed using the robust decrypt algorithm.
A couple of months later, in December, it buried that earlier record with the disclosure that a breach in 2013, by a different group of hackers had compromised 1 billion accounts. Besides names, dates of birth, email addresses, and passwords that did not as well protected as those involved in 2014, security questions and answers were compromised. In October of 2017, Yahoo revised that estimate, saying that all 3 billion user accounts had been compromised.
The breaches knocked an estimated $350 million off Yahoo’s sale price. Verizon eventually paid $4.48 billion for Yahoo’s core Internet business. The agreement called for the two companies to share regulatory and legal liabilities from the breaches. The sale did not include a reported investment in Alibaba Group Holding of $41.3 billion and an ownership interest in Yahoo Japan of $9.3 billion. (Armerding, 2018)
Adult Friend Finder
The Friend Finder Network, which included casual hookup and adult content websites like Adult Friend Finder, Penthouse.com, Cams.com, iCams.com, and Stripshow.com, was breached sometime in mid-October 2016. Hackers collected 20 years of data on six databases that included names, email addresses, and passwords, which were more than 412.2 million. Most of the passwords were protected only by the weak SHA-1 hashing algorithm, which meant that 99 percent of them had been cracked by the time LeakedSource.com published its analysis of the entire data set on November 14. (Armerding, 2018)
eBay
The online auction giant reported a cyber attack in May 2014 that it said exposed names, addresses, dates of birth and encrypted passwords of all its 145 million users. The company said hackers got into the company network using the credentials of three corporate employees, and had complete inside access for 229 days, during which time they were able to make their way to the user database. It asked its customers to change their passwords but said financial information, such as credit card numbers, was stored separately and was not compromised. The company was criticized at the time for lack of communication informing its users and poor implementation of the password-renewal process. (Armerding, 2018)
Equifax
Personal information (including Social Security Numbers, birth dates, addresses, and in some cases drivers’ license numbers) of 143 million consumers; 209,000 consumers also had their credit card data exposed.
Details: Equifax, one of the largest credit bureaus in the U.S., said on Sept. 7, 2017, that an application vulnerability on one of their websites led to a data breach that exposed about 147.9 million consumers. The breach was discovered on July 29, but the company says that it likely started in mid-May. (Armerding, 2018)
Heartland Payment Systems
At the time of the breach, Heartland was processing 100 million payment card transactions per month for 175,000 merchants – most small- to mid-sized retailers. It was not discovered until January 2009, when Visa and MasterCard notified Heartland of suspicious transactions from accounts it had processed. Among the consequences were that Heartland was deemed out of compliance with the Payment Card Industry Data Security Standard (PCI DSS) and was not allowed to process the payments of major credit card providers until May 2009. The company also paid out an estimated $145 million in compensation for fraudulent payments.
A federal grand jury indicted Albert Gonzalez and two unnamed Russian accomplices in 2009. Gonzalez, a Cuban-American, was alleged to have masterminded the international operation that stole the credit and debit cards. In March 2010 he was sentenced to 20 years in federal prison. The vulnerability to SQL injection was well understood, and security analysts had warned retailers about it for several years. The continuing vulnerability of many Web-facing applications made SQL injection the most common form of attack against Web sites at the time. (Armerding, 2018)
Target Stores
The breach began before Thanksgiving but was not discovered until several weeks later. The retail giant initially announced that hackers had gained access through a third-party HVAC vendor to its point-of-sale (POS) payment card readers and had collected about 40 million credit and debit card numbers. By January 2014, however, the company upped that estimate, reporting that personally identifiable information (PII) of 70 million of its customers had been compromised. That included full names, addresses, email addresses, and telephone numbers. The final estimate is that the breach affected as many as 110 million customers. The company recently estimated the cost of the breach at $162 million.
The company was credited with making significant security improvements. However, a settlement announced in May 2017 that gave Target 180 days to make specific security improvements was described by Tom Kellermann, CEO of Strategic Cyber Ventures and former CSO of Trend Micro, as a “slap on the wrist.” He also said it, “represents yesterday’s security paradigm,” since the requirements focus on keeping attackers out and not on improving incident response. (Armerding, 2018)
TJX Companies, Inc
There are conflicting accounts about how this happened. One supposes that a group of hackers took advantage of a weak data encryption system and stole credit card data during a wireless transfer between two Marshall’s stores in Miami. The other has them breaking into the TJX network through in-store kiosks that allowed people to apply for jobs electronically.
Albert Gonzalez, hacking legend and ringleader of the Heartland breach, was convicted in 2010 of leading the gang of thieves who stole the credit cards, and sentenced to 20 years in prison, while 11 others were arrested. He had been working as a paid informant for the US Secret Service, at a $75,000 salary at the time of the crimes. The government claimed in its sentencing memo that companies, banks, and insurers lost close to $200 million. (Armerding, 2018)
Uber
The scope of the Uber breach alone warrants its inclusion on this list, and it is not the worst part of the hack. The way Uber handled the breach once discovered is one big hot mess, and it is a lesson for other companies on what not to do. The company learned in late 2016 that two hackers were able to get names, email addresses, and mobile phone numbers of 57 users of the Uber app. They also got the driver license numbers of 600,000 Uber drivers. As far as we know, no other data such as credit card or Social Security numbers were stolen. The hackers were able to access Uber’s GitHub account, where they found username and password credentials to Uber’s AWS account. Those credentials should never have been on GitHub.
Here’s the sad part: It was not until about a year later that Uber made the breach public. What’s worse, they paid the hackers $100,000 to destroy the data with no way to verify that they did, claiming it was a “bug bounty” fee. Uber fired its CSO because of the breach, effectively placing the blame on him. The breach is believed to have cost Uber dearly in both reputation and money. At the time that the breach was announced, the company was in negotiations to sell a stake to Softbank. Initially, Uber’s valuation was $68 billion. By the time the deal closed in December, its valuation had dropped to $48 billion. Not all the drop is attributable to the breach, but analysts see it being a significant factor. (Armerding, 2018)
JP Morgan Chase
The largest bank in the nation was the victim of a hack during the summer of 2014 that compromised the data of more than half of all US households – 76 million – plus 7 million small businesses. The data included contact information – names, addresses, phone numbers, and email addresses – as well as internal information about the users, according to a filing with the Securities and Exchange Commission. The bank said no customer money had been stolen and that there was “no evidence that account information for such affected customers – account numbers, passwords, user IDs, dates of birth or Social Security numbers – was compromised during this attack.” Still, the hackers were reportedly able to gain “root” privileges on more than 90 of the bank’s servers, which meant they could take actions including transferring funds and closing accounts. According to the SANS Institute, JP Morgan spends $250 million on security every year.
In November 2015, federal authorities indicted four men, charging them with the JP Morgan hack. Gery Shalon, Joshua Samuel Aaron and Ziv Orenstein faced 23 counts, including unauthorized access of computers, identity theft, securities and wire fraud and money laundering that netted them an estimated $100 million. A fourth hacker who helped them breach the networks was not identified. Shalon and Orenstein, both Israelis, pleaded not guilty in June 2016. Aaron was arrested at JFK Airport in New York last December. (Armerding, 2018)
US Office of Personnel Management (OPM)
Hackers, said to be from China, were inside the OPM system starting in 2012, but were not detected until March 20, 2014. A second hacker, or group, gained access to OPM through a third-party contractor in May 2014 but was not discovered until nearly a year later. The intruders exfiltrated personal data – including in many cases detailed security clearance information and fingerprint data of 22 million current and former federal employees. Former FBI director James Comey spoke of the information contained in the so-called SF-86 form, used for conducting background checks for employee security clearances. “My SF-86 lists every place I have ever lived since I was 18, every foreign travel I have ever taken, all of my family, their addresses,” he said. “So, it is not just my identity that’s affected. I have got siblings. I have got five kids. All of that is in there.”
A report, released by the House Committee on Oversight and Government Reform summed up the damage in its title: “The OPM Data Breach: How the Government Jeopardized Our National Security for More than a Generation.” (Armerding, 2018)
Anthem
The second-largest health insurer in the U.S., formerly known as WellPoint, said a cyber attack had exposed the names, addresses, Social Security numbers, dates of birth and employment histories of 78.8 million current and former customers – everything necessary to steal an identity. Fortune reported in January that a nationwide investigation concluded that a foreign government likely recruited the hackers who conducted what was said to be the most significant data breach in healthcare history. It reportedly began a year before it was announced, when a single user at an Anthem subsidiary clicked on a link in a phishing email. The total cost of the breach is not yet known, but it is expected to exceed $100 million. Anthem said in 2016 that there was no evidence that members’ data have been sold, shared or used fraudulently. Credit card and medical information also allegedly has not been taken. (Armerding, 2018)
RSA Security
The impact of the cyber attack that stole information of Possibly 40 million employee records on the security giant’s SecurID authentication tokens is still being debated. RSA, the security division of EMC, said two separate hacker groups worked in collaboration with a foreign government to launch a series of phishing attacks against RSA employees, posing as people the employees trusted, to penetrate the company’s network.
EMC reported last July that it had spent at least $66 million on remediation. According to RSA executives, no customers’ networks were breached. John Linkous, vice president, chief security and compliance officer of eIQnetworks, Inc. does not buy it. “RSA did not help the matter by initially being vague about both the attack vector, and (more importantly) the data that was stolen,” he says. “It was only a matter of time before subsequent attacks on Lockheed-Martin, L3, and others occurred, all of which are believed to be partially enabled by the RSA breach.” Beyond that was psychological damage. Among the lessons, he said, are that even good security companies like RSA are not immune to being hacked. (Armerding, 2018)
VeriSign
Security experts are unanimous in saying that the most troubling thing about the VeriSign breach, or breaches, in which hackers gained access to privileged systems and information, is the way the company handled it – poorly. VeriSign never announced the attacks. The incidents did not become public until 2011, and then only through a new SEC-mandated filing.
As PCWorld put it, “VeriSign buried the information in a quarterly Securities and Exchange Commission (SEC) filing as if it was just another mundane tidbit.”
VeriSign said no critical systems such as the DNS servers or the certificate servers were compromised but did say that “access was gained to information on a small portion of our computers and servers.” It has yet to report what the information stolen was and what impact it could have on the company or its customers. (Armerding, 2018)
Home Depot
The hardware and building supply retailer announced in September what had been suspected for some weeks – that beginning in April or May 2014, its POS systems had been infected with malware. The company later said an investigation concluded that a “unique, custom-built” malware had been used, which posed as anti-virus software. In March 2016, the company agreed to pay at least $19.5 million to compensate US consumers through a $13 million fund to reimburse shoppers for out-of-pocket losses and to spend at least $6.5 million to fund 1 1/2 years of cardholder identity protection services.
The settlement covers about 40 million people who had payment card data stolen and more than 52 million people who had email addresses stolen. There was some overlap between the groups. The company estimated $161 million of pre-tax expenses for the breach, including the consumer settlement and expected insurance proceeds. (Armerding, 2018)
Adobe
Originally reported in early October by security blogger Brian Krebs, it took weeks to figure out the scale of the breach and what it included. The company originally reported that hackers had stolen nearly 3 million encrypted customer credit card records, plus login data for an undetermined number of user accounts. Later in the month, Adobe said the attackers had accessed IDs and encrypted passwords for 38 million “active users.” However, Krebs reported that a file posted just days earlier, “appears to include more than 150 million usernames and hashed password pairs taken from Adobe.” After weeks of research, it eventually turned out, as well as the source code of several Adobe products, the hack had also exposed customer names, IDs, passwords and debit and credit card information.
In August 2015, an agreement called for Adobe to pay a $1.1 million in legal fees and an undisclosed amount to users to settle claims of violating the Customer Records Act and unfair business practices. In November 2016, the amount paid to customers was reported at $1 million. (Armerding, 2018)
Cyber attackers stole data from 29 million Facebook accounts using an automated program that moved from one friend to the next, Facebook Inc (FB. O) announced on Friday, as the social media company said its largest-ever data theft hit fewer than the 50 million profiles it initially reported. The company said it would message affected users over the coming days to tell them what type of information had been accessed in the attack. The breach has left users more vulnerable to targeted phishing attacks and could deepen unease about posting to a service whose privacy, moderation and security practices have been called into question by a series of scandals, cybersecurity experts and financial analysts said. The attackers took profile details such as birth dates, employers, education history, religious preference, types of devices used, pages followed and recent searches and location check-ins from 14 million users.
For the other 15 million users, the breach was restricted to name and contact details. Also, attackers could see the posts and lists of friends and groups of about 400,000 users.
The vulnerability the hackers exploited existed from July 2017 through late last month, when Facebook noticed an unusual increase in the use of its “view as” feature. That feature allows users to check privacy settings by glimpsing what their profile looks like to others. However, three errors in Facebook’s software enabled someone accessing “view as” to post and browse from the Facebook account of the other user. The attackers used the “view as” flaw with “a small handful” of accounts they controlled to capture data of their Facebook friends, then used a tool they developed to breach friends of friends and beyond, Rosen said. Facebook patched the issue last month and asked 90 million users to log back into their accounts, many just as a precaution. (Vengattil, and Dave, 2018)
Exactis
Exactis, a data broker based in Palm Coast, Florida, had exposed a database that contained close to 340 million individual records on a publicly accessible server. The haul comprises close to 2 terabytes of data that appears to include personal information on hundreds of millions of American adults, as well as millions of businesses. While the precise number of individuals included in the data is not precise—and the leak does not seem to contain credit card information or Social Security numbers—it does go into minute detail for each listed, including phone numbers, home addresses, email addresses, and other highly personal characteristics for every name. The categories range from interests and habits to the number, age, and gender of the person’s children. Exactis has two versions of the database, one of which appears to have been newly added during the period he was observing its server. Both contained roughly 340 million records, split into about 230 million records on consumers and 110 million on business contacts. On its website, Exactis boasts that it possesses data on 218 million individuals, including 110 million US households, as well a total of 3.5 billion “consumer, business, and digital records.” (Greenberg, 2018)
Reference
Climer, Siobhan. (2018, November). History of Cyber Attacks from Morris worm to exactis, Mindsight retrieved from https://www.gomindsight.com/blog/history-of-cyber-attacks-2018/
Price, David. (2008, June 30). Blind Whistling Phreaks and the FBI’s Historical Reliance on Phone Tap Criminality. Counterpunch retrieved from https://web.archive.org/web/20080701125121/http://www.counterpunch.org/price06302008.html
Rosenbaum, Ron. (2011, Oct 7). “Secrets of the Little Blue Box.” SLATE Retrieved from http://www.slate.com/articles/technology/the_spectator/2011/10/the_article_that_inspired_steve_jobs_secrets_of_the_little_blue_.html
Delio, Michelle. (2002, May 05). Mitnick’s ‘Lost Chapter’ Found. WIRED Retrieved from https://www.wired.com/2002/11/mitnicks-lost-chapter-found/
Mclellan, Vin. (1981, July 26). Case of the Purloined Password. The New York Times
Retrieved from https://www.nytimes.com/1981/07/26/business/case-of-the-purloined-password.html?pagewanted=3&pagewanted=all
Delio, Michelle, (2001, June 02). The Greatest Hacks of All Time. WIRED Retrieved from https://www.wired.com/2001/02/the-greatest-hacks-of-all-time/?currentPage=all
Los Angeles: Hackers Gets 51 months in Radio Contest Scam. (1995, April 11). Los Angeles Times Retrieved from http://articles.latimes.com/1995-04-11/local/me-53388_1_los-angeles-radio-stations
Elmer-DeWitt, Philip. (1983, August 29). The 414 Gang Strikes Again. Time. p. 75. retrieved from http://content.time.com/time/magazine/article/0,9171,949797,00.html”Beware: Hackers at play.” Newsweek. September 5, 1983. Pp. 42–46, 48.
Wikipedia contributors. (2018, October 30). List of security hacking incidents. In Wikipedia, The Free Encyclopedia. Retrieved 19:43, November 2, 2018, from https://en.wikipedia.org/wiki/List_of_security_hacking_incidents
Hackers jam Microsoft’s site. (1997, June 20). CNET Retrieved from https://www.cnet.com/news/hackers-jam-microsofts-site/
Mckay, Niall. (1998, September 10). Pentagon Deflects Web Assault. WIRED Retrieved from https://www.wired.com/1998/09/pentagon-deflects-web-assault/
Joybubbles – Wikipedia. (n.d.). Retrieved from https://en.wikipedia.org/wiki/Joybubbles
Lancaster Eagle-gazette From Lancaster, Ohio On December … (n.d.). Retrieved from https://www.newspapers.com/newspage/297600840/
List Of Notable Security Hacking Incidents – Wikipedia. (n.d.). Retrieved from https://en.wikipedia.org/wiki/List_of_notable_security_hacking_incidents
Hackers Leave Ransom Note on Yahoo Site (December 10, 1997), Los Angeles Times Retrieved from http://articles.latimes.com/1997/dec/10/business/fi-62418
Krebs, B (2005). Teen Pleads Guilty to hacking Paris Hilton’s phone. Washington Post. Retrieved from http://www.washingtonpost.com/wp-dyn/content/article/2005/09/13/AR2005091301423.html?noredirect=on
Vause, John. (March 11,2008). Chinese Hackers: No site is safe. CNN. Retrieved from http://edition.cnn.com/2008/TECH/03/07/china.hackers/index.html
Hoffman, Stefanie. (March 14,2008). Trend Micro Victim of Malicious Hack. CRN. Retrieved from https://www.crn.com/news/security/206903880/trend-micro-victim-of-malicious-hack.htm
Kumar, Mohit. (2011, March 26). Thousands of Bank of America Accounts Hacked! The Hacker News. Retrieved from https://thehackernews.com/2011/03/thousands-of-bank-of-america-accounts.html
Chung, Emily (2011, Apr 27), PlayStation data breach deemed in ‘top 5 ever’. CBC. retrieved from https://www.cbc.ca/news/technology/playstation-data-breach-deemed-in-top-5-ever-1.1059548
Breach halts electronic pay stubs for federal workers (2011, April 19), CBC. Retrieved from https://www.cbc.ca/news/canada/breach-halts-electronic-pay-stubs-for-federal-workers-1.1086030
Armerding, Taylor (2018, Jan 26), The 17 Biggest data Breaches of the 21st Century. CSO online. Retrieved from https://www.csoonline.com/article/2130877/data-breach/the-biggest-data-breaches-of-the-21st-century.html
Vengattil, Munsif and Dave, Paresh (2018, October 12), Facebook now says data breach affected 29 million users, details impact. REUTERS. Retrieved from https://www.reuters.com/article/us-facebook-cyber/facebook-now-says-data-breach-affected-29-million-users-details-impact-idUSKCN1MM297?feedType=RSS&feedName=topNews
Greenberg, Andy (2018, June 27), Marketing Firm Exactis leaked a personal info Database with 340 Million Records. WIRED Retrieved from https://www.wired.com/story/exactis-database-leak-340-million-records/
Andress, Jason, and Winterfeld, Steve (2014). Cyber warfare: Techniques, tactics, and tools for security practitioners (pp. 35-179). Syngress, Waltham, Ma. (ISBN: 9780124166721). Available in the Trident Online Library.
Dordal, Peter L. (2017). An introduction to computer networks. The book under Creative Commons
McIIwraith, Angus (2006). Information security and employee behavior: How to reduce risk through employee education, training, and awareness. Gower, Aldershot, England. ISBN (978-0-566-08647-2). Available in the Trident Online Library.
Risk management for enterprises and individuals (2017) Book under Creative Commons
Simmons, Andrea C. (2012). Once more unto the breach: Managing information security in an uncertain world. Ely, Cambridgeshire, IT Governance Publishing. ISBN (9781849283885). Available in the Trident Online Library.
Vacca, John R. (2013). Computer and information security handbook. Morgan Kaufmann, Amsterdam. ISBN (9780123943972). Available in the Trident Online Library.
Vacca, John R. (2014). Managing information security. Syngress, Waltham, Ma. ISBN (9780124166882). Available in the Trident Online Library.
Woody, Aaron (2013). Enterprise security: A data-centric approach to securing the enterprise. Packt, Birmingham, UK. ISBN (9781849685962).
Soper, Daniel (2017). Information Privacy and Security. Security Lesson #3 Software Program Security https://www.youtube.com/watch?v=AeFyCGpclwY&list=PLlYw7XsK0HV-r0T5fypBv9-a1gbq8xkZR&index=3
Soper, Daniel (2017). Information Privacy and Security. Security Lesson #4 Malicious Code – Malware https://www.youtube.com/watch?v=wn-uVP8HncA&list=PLlYw7XsK0HV-r0T5fypBv9-a1gbq8xkZR&index=4
Soper, Daniel (2017). Information Privacy and Security. Security Lesson #5 – Illicit Data Interception and Access https://www.youtube.com/watch?v=F_obVu9HknQ&list=PLlYw7XsK0HV-r0T5fypBv9-a1gbq8xkZR&index=5























viagra purchase online what is the ingredients in viagra viagra web sites