In today’s world, there are millions of unsecured computer networks in continuous communication with each other. The growing threat of cyber-attacks has made governments and companies more aware of the need to defend the computer-controlled control systems of utilities and other critical infrastructure. When it comes to data breaches, the risk for government and companies is high, from the easily calculable costs of notification and business loss to the less tangible effects on an organization’s brand and customer loyalty. With the growing number of worms, viruses, stealing of intellectual properties, hackers, nation-states engaging in information warfare and malicious insiders-combined with the new millennium exploding regulatory environment-organizations are adopting best of breed security infrastructures model to protect themselves, organization and customers.
In addition to proprietary and compliance issues, the prevalence and damage caused by attacks have grown to staggering proportions. These attacks are not only increasing in frequency but complexity and severity as well. The time-to-exploitation of today’s most sophisticated worms and viruses has shrunk from years to months to days, and in some cases, to a matter of hours. Defending against these attacks is becoming more difficult in a short period. It is not just external attacks that organizations must defend against, but malicious insiders who aim to steal confidential internal, customer and business data and sell it to outsiders for their financial gain.
Per the recent study, financial institutions are victims of insider attacks. Also, many companies overseas are not even aware that cybercriminals have attacked them. Also, Insider attacks become a severe threat to organizations due to emerging technologies such as cloud computing that provides computing as a utility that has attracted organizations to store their sensitive data remotely by subscribing to the virtual storage from the cloud services provider. This Assignment will highlight how The Committee of National Security System can help to reduce malicious insider threats in the organization.
Background
Year by year the importance of Information Security (InfoSec) and Information Assurance (IA) grows. In 2018, security budgets received higher priority worldwide compare with 2017. The spending on security is expected to grow from $101 billion in 2017 to $124 Billion in 2019, an increase of 12.4 percent from last year, according to the latest forecast from Gartner, Inc. In 2019, the market is forecast to grow 8.7 percent to $124 billion [1].
Worldwide Security Spending by Segment, 2017-2019 (Millions of U.S. Dollars) **
| Market Portion | 2017 Data | 2018 Data | 2019 Data |
| Application Security | 2,434 | 2,742 | 3,003 |
| Cloud Security | 185 | 304 | 459 |
| Data Security | 2,563 | 3,063 | 3,524 |
| Identity Access Management | 8,823 | 9,768 | 10,578 |
| Infrastructure Protection | 12,583 | 14,106 | 15,337 |
| Integrated Risk Management | 3,949 | 4,347 | 4,712 |
| Network Security Equipment | 10,911 | 12,427 | 13,321 |
| Other Information Security Software | 1,832 | 2,079 | 2,285 |
| Security Services | 52,315 | 58,920 | 64,237 |
| Consumer Security Software | 5,948 | 6,395 | 6,661 |
| Total | 101,544 | 114,152 | 124,116 |
Source: Gartner (August 2018)
Gartner has identified key trends affecting information security spending in 2018-2019
The Definition of InfoSec and IA
The term InfoSec and IA are often interpreted differently and are adopted from [2] where they are elaborated by the detailed analysis. The definitions of InfoSec and IA in this assignment are outlined below (throughout the text all important definitions are italicized).
1. Information Security
InfoSec is a multidisciplinary area of study and professional activity which is concerned with the development and implementation of security countermeasures of all available types (technical, organizational, human-oriented and legal) in order to keep information in all its locations (within and outside the organization’s perimeter) and, consequently, information systems, where information is created, processed, stored , transmitted and destructed, free from threats[2].
2. Information Assurance
IA is a multidisciplinary area of study and professional activity that aims to protect the business by reducing risks associated with information and information systems using comprehensive and systematic management of security countermeasures, which is driven by risk analysis and cost-effectiveness [2].
Here I refer to the Information Assurance & Security (IAS) knowledge area [2], this includes all actions directed at keeping information secure as well as the management of these actions. Information Security is now no longer the sole responsibility of a discrete group of people in the company, but it is the responsibility of every employee, especially manger from top to bottom or bottom to the top level.
What is Security?
Security is “the quality or state of being secure – to be free from danger [3].” in other words, it protects adversaries, harm, worms, and attacks, intentionally or otherwise – is the objection.
Security is often achieved by different means of several planning and strategies undertaken simultaneously or used in combination with one another. For example, National Security is a multilayered system, which protects, its assets, its resources, its people and the sovereignty of a state.
Specialized areas of security
Achieving the appropriate level of security for an organization also requires a multifaceted system. A success organization should have the following multiple layers of security in place to protect its operations;
- Physical Security: It is to protect physical items, objects, or areas from unauthorized access and misuse
- Personal Security: It is to protect the individual or group of individuals who are authorized to access the organization and its operations
- Operation Security: It is to protect the details of the operation or a series of activities.
- Communication Security: It is to communications media, technology, and content.
- Network Security: It is to protect networking components, connections, and contents.
- Information Security: it is the protection of information and its critical elements (Confidentiality, Integrity, and availability), including the systems and hardware that use, store, and transmit that information through the application of policy, education, technology, training, and awareness program.
The Committee on National Security Systems (CNSS)
CNSS defines information security as the protection of information and its critical elements, including the systems and hardware that use, store, and transmit that information [4]. The CNSS Model of information security evolved from a concept developed by the computer security industry called the C.I.A triangle. Figure 1-1 shows that information security includes broad areas of information security management, computer and tata security, and network security.
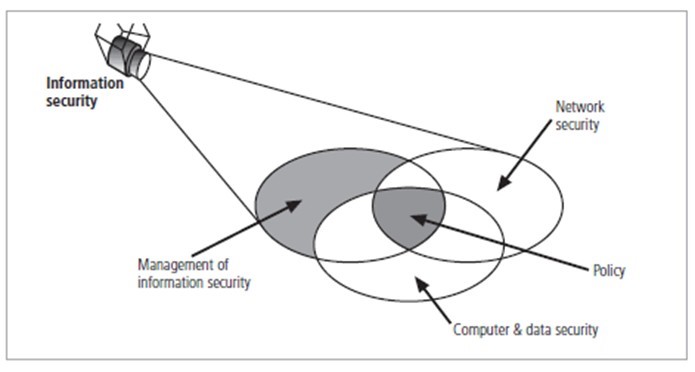
C.I.A Triad/Triangle
The C.I.A triangle has been the industry standard for computer security since the development of the mainframe. It’s based on the three characteristics of information that give it value to the organization.
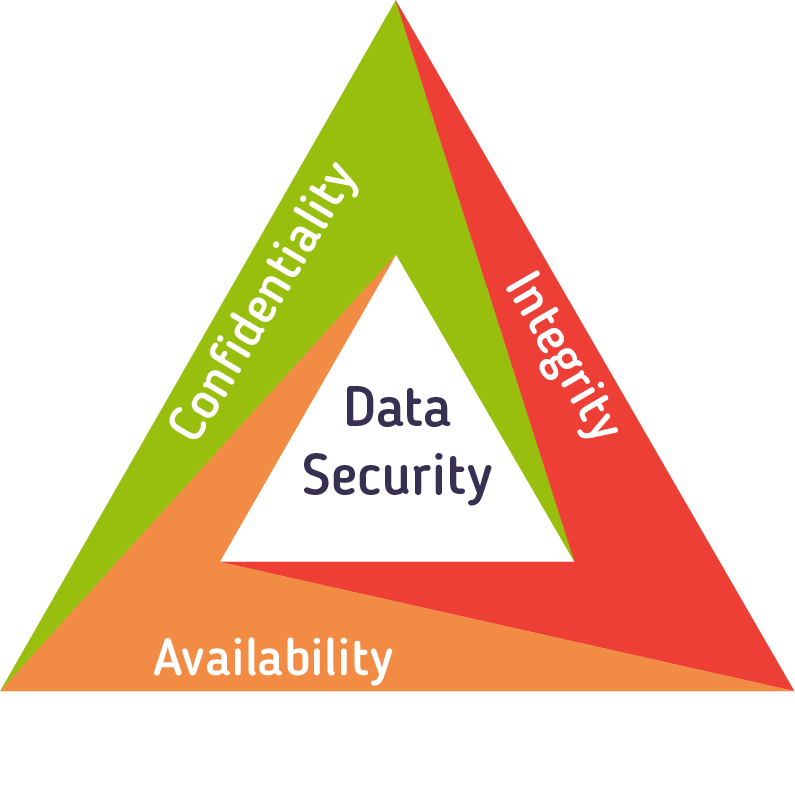
Critical Characteristics of Information
It is based on three major characteristics of information in the beginning, and now it has expanded into a more comprehensive list of critical characteristics of information.
- Confidentiality: Another term for confidentiality would be privacy. Company policies should restrict access to the information to authorized personnel and ensure that only those authorized individuals view this data. The data may be compartmentalized according to the security or sensitivity level of the information. Misuse.
For example, the machine operator should not have to access, the personal information of all employees. Furthermore, employees should receive training to understand the best practices in safeguarding sensitive information to protect themselves and the organization from attacks.
The best method used here to ensure confidentiality is to include data encryption, username ID and password, Two Factor Authentication, and minimizing exposure of sensitive information.
- Integrity: Integrity is the name of Accuracy, consistency, and trustworthiness of the data during its entire life cycle. Here we make sure that data must be unaltered during the transit and is not changed by unauthorized entities.
how to ensure data integrity?
- File permissions and user access control can prevent unauthorized access.
- Version control can be used to prevent accidental changes by authorized users.
- The backup must be available to restore any corrupted data
- Checksum hashing can be used to verify the integrity of the data during transfer
- A checksum is used to verify the integrity of files or strings of characters after they have been transferred from one device to another across your local network or the internet.
- For Example: If you forget your password, your password cannot be recovered from hashed value. They must be reset.
- If you downloaded a file, you could verify its integrity by verifying the hash values from the source with the one you generated using any hash calculator. By comparing the hash values, you can ensure that the file has not been tampered with or corrupted during the transfer.
- Availability: The Characteristic of information that enables user access to information in a required format, without interference or obstruction. A user in this definition may be either a person or another computer system.
- For Example, This includes maintaining equipment, performing hardware repairs, keeping operating systems and software up-to-dates, and creating backups ensure the availability of the network and data to the authorized users. Plans should be in place to recover quickly from natural or human-made disasters. Security equipment or software, such as firewalls, guard against downtime because of attacks, such as the denial of service (DoS). Denial of service occurs when an attacker attempts to overwhelm resources, so the services are not available to the users.
- Privacy: The Information that is collected, used, and stored by an organization is to be used only for the purpose stated to the data owner at the time it was collected. This definition of privacy does focus on freedom from observation but rather means that information will be used only in a way known to the person providing it.
- Identification: An information system possesses the characteristic of identification when it recognizes individual users. Identification and authentication are essential to establishing the level of access or authorization that an individual is granted.
- Authentication: Authentication occurs when a control provides proof that a user possesses the identity that he or she claims. In computing, e-Business and information security, it is necessary to ensure that the data, transactions, communications or documents (electronic or physical) are genuine or they have not been forged or fabricated.
- Authorization: After the identity of a user is authenticated, a process called authorization provides assurance that the user (whether a person or a computer) has been specifically and explicitly authorized by the proper authority to access, update or can delete the contents of information assets. The user could be a person or a computer.
- Accountability: The Characteristic of accountability exists when a control provides assurance that every activity undertaken can be attributed to a named person or automated process. For example, audit logs that track user activity on an information system provide accountability.
- Accuracy: information should have accuracy. The information has accuracy when it is free from mistakes or errors, and it has the value that the end-users expect. If the information contains a value different from the user’s expectations, due to the intentional or unintentional modification of its content, it is no longer accurate.
- Utility: The utility of information is the quality of having value for some end purpose. If the information is available but is not in a format meaningful to the end-user, it is not useful. For example, US Census data can difficult to interprets for a private citizen as compared to politicians. To the politician, it can reveal information related to his next campaign.
- Possession: The possession of information security is the quality or state of having ownership or control of some object or item.
NSTISSC Security Model
‘National Security telecommunications & information systems security committee.‘ It is now called the National Training Standard for Information Security Professional. This security model is a comprehensive model of InfoSec known as the McCumbers cube created in 1991, which is named after a developer, John McComber. It is becoming standard to determine the characteristics, location, and security of the information. It is a three-dimension model. These three dimensions are represented in a cube with 27 cells with each cell representing each aspect of information.
The cells that can be represented are the below
- Confidentiality, Integrity, availability
- Policy, Education, Technology
- Storage, Processing, Transmission
The McCumbers Cube in figure 1-5, shows three dimensions with each axis become a 3x3x3 cube with 27 cells representing areas that must be addressed to secure today’s information systems. Each of the 27 areas must be properly addressed during the security process,
For example
The intersection between technology, integrity, and storage requires control or safeguard that addresses the need to use technology to protect the integrity of information while in storage. One such control might be a system for detecting host intrusion that protects the integrity of information by alerting the security administrators to the potential modification of critical files.
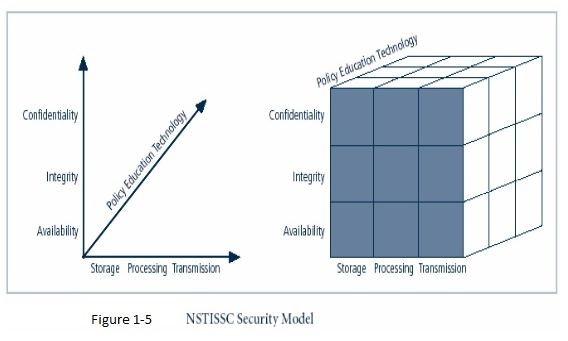
What is commonly left out of such model is the need for guidelines and policies that provide direction for the practices and implementations of technologies.
Components of an Information System
– Software – Hardware – Data
– People – Procedures – Networks
- Software
The software components of Information System (IS) comprise applications, operating systems, and assorted command utilities. Software programs are the vessels that carry the lifeblood of information through an organization. These are often created under the demanding constraints of project management, which limit time, cost, and workforce.
- Hardware
Hardware is the physical technology that executes the software, store and carries the data, and provides interfaces for the entry and removal of information from the system. Physical security policies deal with hardware as a physical asset and with the protection of these physical assets from harm or theft. Applying the traditional tools of physical security, such as locks and keys, restricts access to and interaction with the hardware components of any information system. Securing the physical location of computers and the computers themselves is important because a breach of physical security can result in a loss of information. Unfortunately, most information systems are built on hardware platforms that can’t guarantee any level of information security if unrestricted access to the hardware if possible.
- Data
- Stored data, processed, and transmitted through a computer system must be protected
- Data is often the most valuable asset possessed by an organization and is the main target of intentional attacks.
- The raw, unorganized, isolated potentially useful facts and figures that are later processed and manipulated to produce information.
- People
There are many roles for people in information systems. common ones include
- System Analyst
- Programmer
- Technician
- Engineer
- Network manager
- MIS (Manager of Information Systems)
- Data Entry Operator
- Procedure
A procedure is a series of documented actions taken to achieve something. A procedure is more than a single simple task. A procedure can be quite complex and involved, such as performing a backup, shutting down a system, patching software.
- Networks
- When Information Systems are connected to form Local Area Network (LANs), and these LANs are connected to other networks such as the internet, new security challenges rapidly emerge.
- Steps to provide network security are essential, as is the implementation of the alarm and intrusion system to make system owners aware of ongoing compromises.
Securing Components
Protecting the components from potential misuse and abuse by unauthorized users, where the computer is used as an active tool to conduct the attack or computer itself is the entity being attacked.
There are two types of attacks
- Direct Attack: When a hacker uses his personal computer to break into as systems.
- Indirect Attack: When a system is compromised and used to attack another system.
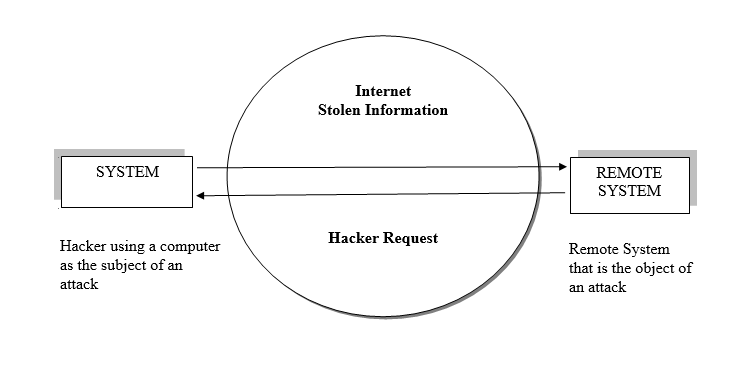
A computer can, therefore, be both the subject and object of an attack, For Example, if Remote system an attack on the system and then system compromised and then used that system to an attack another system, at which point it becomes the more vulnerable object of attack of an attack,
Balancing Information Security and Access
- Information Security can’t be absolute: it is processed, not a goal
- Must provide the security and is also feasible to access the information for its application
- Should balance protection and availability.
Approaches to Information Implementation
- Bottom-up-approach
- Top-down approach
- It has a higher probability of success.
- The project is initiated by upper-level managers who issue policy & procedures and processes.
- Dictate the goals & expected outcomes of the project.
- Determine who is suitable for each of the required actions.
SDLC Waterfall methodology
SDLC – is a methodology for the design and implementation of an information system in an organization.
- A methodology is a formal approach to solving a problem based on a structured sequence of procedures.
- SDLC consists of 6 phases.
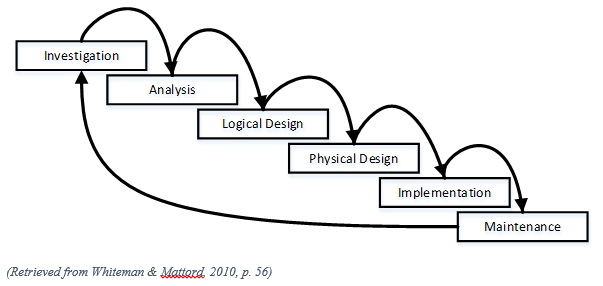
Investigation: It is the most important phase, and it begins with an examination of the event or plan that initiates the process. During the phase, the objectives, constraints, and scope of the project are specified. At the end of this phase, a feasibility analysis is performed, which assesses the economic, technical and behavioral feasibilities of the process and ensures that implementation is worth the organization’s time and effort.
Analysis: It begins with the information gained during the investigation phase. It consists of the quality of the organization, the status of current systems, and the capability to support the proposed systems. Analysts begin by determining what the new system is expected to do, and how it will interact with existing systems.
Logical Design: In this phase, the information gained from the analysis phase is used to begin creating a systems solution for the business problem. Based on business needs, applications are selected that can provide needed services. Based on the applications needed, data support and structures capable of providing the needed inputs are then chosen. In this phase, analysts generate several alternative solutions, each with corresponding strengths and weaknesses, and cost and benefits. At the end of this phase, another feasibility analysis is performed.
Physical design: In this phase, specific technologies are selected to support the solutions developed in the logical design. The selected components are evaluated based on a make or buy decision. The final design integrates various components and technologies.
Implementation: In this phase, any needed software is created. Components are ordered, received and tested Afterwards; users are trained and supporting documentation created. Once all the components are tested individually, they are installed and tested as a system. Again, a feasibility analysis is prepared, and the sponsors are then presented with the system for a performance review and acceptance test.
Maintenance and change: It is the longest and most expensive phase of the process. It consists of the tasks necessary to support and modify the system for the remainder of its useful life cycle. Periodically, the system is tested for compliance, with business needs. Upgrades, updates, and patches are managed. As the needs of the organization change, the systems that support the organization must also change. When a current system can no longer support the organization, the project is terminated, and a new project is implemented.
Security Professionals and the organization
- Senior Management Chief information office (CIO) is responsible for the assessment, management, and implementation of information security in the organization.
- Information Security Project Team
- Champion: they promote the project to ensure its support, both financially and administratively.
- Team Leader: they understand project management, personnel management, and informational security technical requirements.
- Security policy developers: such individuals who understand the organizational culture, existing policies and requirements for developing and implementing successful policies.
- Risk assessment specialists: these are those individuals who understand financial risk assessment techniques, the value of organizational assets and the security method to be used.
- Security Professionals: they should be dedicated, trained, and well-educated specialists in all aspects of information security from both a technical standpoint.
- System Administrators: they are administrating the systems that house the information used by the organization.
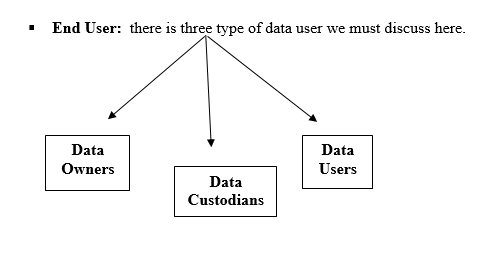
- Data Owners: They are responsible for the security and use of a set of information. They are also responsible to determine the level of data classification. They work with subordinate managers to oversee the day-to-day administration of the data.
- Data Custodians: they are responsible for the storage, maintenance, and protection of the information. They have to oversee data storage and backups, implementing the specific procedures and policies.
- Data Users: they work with the information to perform their daily jobs supporting the mission of the organization. Everyone in the organization is responsible for the security of data, so data users are included here as individuals with an information security role.
CNSS Model for University Security
The Basic objectives of CNSS/NSTISSC model are to secure data in 3 probable ways:
- Using security services
- Maintaining information states
- Setting security countermeasures
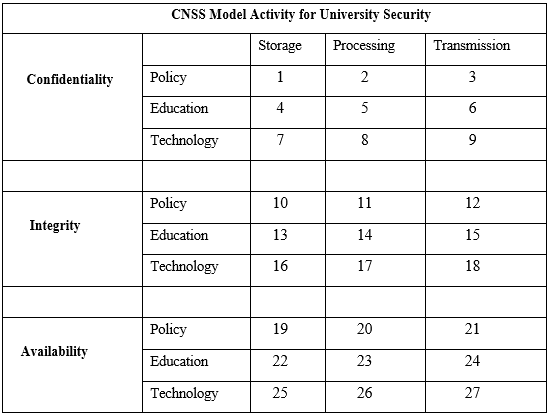
- Confidentiality-Policy and Storage: in this process, the University has certain policies and guidelines for an enrolled student and staff. All the relevant data associated is kept confidential only accessible to authorized personnel only, and a secure storage solution is provided by the University to safeguard its and student’s data.
- Confidentiality-Policy and Processing: in this process, an authorized person is appointed to process data whenever required. That person must maintain the confidentiality of data and work according to university policies. The example here I can put is, I am submitting this assignment electronically to my lecturer only.
- Confidentiality-Policy and Transmission: in this process only keeping data confidential and personal working under policies is not enough as a secure medium is required for transmission of that data when a user requests to access. The university is required to use all necessary measures to secure a transmission.
- Confidentiality-Education and Storage: only a student enrolled subject should get the subject materials of the enrolled subject. That is the use of educational data and storage of material should be kept confidential for the actual students not all.
- Confidentiality-Education and Processing: the lecturer needs to update slides or educational materials constantly updates any new materials and sent to the subject enrolled students.
- Confidentiality-Education and transmission: Data and information related to the subject be kept secure by applying a range of measures like only enrolled students attend classes as card swap will only open lecture room doors.
- Confidentiality-Technology and Storage: the use of a database system to store and transfer data to only students that are to use.
- Confidentiality-Technology and Processing: Advance processing system as the speed of text collect data and store in the university database. This method maintains confidentiality as the system automatically integrates data from one to another form.
- Confidentiality-Technology and Transmission: The use of optical fiber to transfer data between terminals decreases chances of data being stolen, corrupt, similarly using cryptography in transmission ensures secure data.
- Integrity-Policy and Storage: Data to be uploaded in the electronic format, lecturer and university personal should check the files for corrupted or damaged. The policy to upload files should be maintained.
- Integrity-policy and processing: processing should be done by a person that is aware of university policies and is knowledgeable enough not to do mistakes in data while processing.
- Integrity-Policy and Transmission: The correct electronic data is accessible to students at a time using wired or wireless methods.
- Integrity-Education and Storage: The lecture provides up-to-date data on the university database for students to use it without any mistakes on the information they get.
- Integrity-Education and processing: Educational data and material while processing should not be altered and checked before finalizing upload to the system.
- Integrity-Education-Transmission: only the accurate and useful data be uploaded to the student database as no incorrect data lead to a problem in university.
- Integrity-Technology and Storage: The Subject materials related to a particular subject is stored in the university database system after being checked and verified as correct and useful to students.
- Integrity-Technology and Processing: Some system or software is used to check uploading data for its authenticity.
- Integrity-Technology and transmission: the data on the university network should be correct and be available only after finalizing its integrity of use.
- Availability-Policy and Storage: The university students should get the data any time from the university database. The data should comply with all the rules and policies set by the university.
- Availability-Policy and Processing: The data on the university system should be allowed to be edited by a responsible person whenever some issues are found on available data.
- Availability-Policy and Transmission: change in data by the lecturer on their subject should be immediately available to use by students and should not violate any rules and policies.
- Availability-Education and Storage: Material stored in the university database needs to be updated and ready to use by a student at any moment.
- Availability-Education and Processing: If any changes are to be made in lecture slides or any data. Authorized personnel needs to access it and ready to be used.
- Availability-Education and Transmission: always ready to use data should be in the system so that students can utilize and download whenever they require.
- Availability-Technology and Storage: All necessary documents related to student store in the university database system after being checked and verified as correct, so the student can utilize and download flawlessly
- Availability-Technology and Processing: The data on the university system should be available to be edited by a responsible person whenever an issue is found on available data.
- Availability-Technology and Transmission: All necessary documents need to be accessible to students and lecturers to download or modify based on privileges at any time they want.
References
[1] Moore, Susan. Worldwide Information Security Spending – Gartner Inc August 2018 – https://www.gartner.com/en/newsroom/press-releases/2018-08-15-gartner-forecasts-worldwide-information-security-spending-to-exceed-124-billion-in-2019
[2] Y. Cherdantseva, and J. Hilton, “Information Security and Information Assurance. The Discussion about the Meaning, Scope, and Goals,” in F. Almeida, and I. Portela (eds.),
Organizational, Legal, and Technological Dimensions of IS Administrator. IGI Global Publishing, September 2013.
[3] Merriam-webster. ” Security.” Merriam-webster online. Accessed 18 October 2018 from www.m-w.com/dictionary/security
[4] National Security Telecommunications and Information Systems Security. National
Training Standard for Information Systems Security (Infosec) Professionals. 20 June 1994. File, 4011. Accessed 19 October 2018 from https://www.cnss.gov/CNSS/openDoc.cfm?k46makKdIHkjCCJxnWRZnA==
Andress, Jason, and Winterfeld, Steve (2014). Cyber warfare: Techniques, tactics, and tools for security practitioners. Syngress, Waltham, Ma. (ISBN: 9780124166721) Ch, 1 & 2.
Dordal, Peter L. (2017). An introduction to computer networks. The book under Creative Commons Ch 1-9
Krause, Michael (2010). Managing information security breaches: Studies from real life. Ely, UK, IT Governance Publishing. (ISBN: 9781849280945) Ch 1 & 2.
McIIwraith, Angus (2006). Information security and employee behavior: How to reduce risk through employee education, training and awareness. Gower, Aldershot, England. ISBN (978-0-566-08647-2).
Radović, Vesela and Čaleta, Denis (2014). Comprehensive approach As ‘Sine Qua Non’ for critical infrastructure protection. IOS Press, Amsterdam. ISBN (9781614994770) Part 1.
Simmons, Andrea C. (2012). Once more unto the breach: Managing information security in an uncertain world. Ely, Cambridgeshire, IT Governance Publishing. ISBN (9781849283885) Ch 1 & 2.
Vacca, John R. (2014). Managing information security. Syngress, Waltham, Ma. ISBN (9780124166882) L 1.
Watkins, Steve (2013). An introduction to information security and ISO 27001. IT Goverance Publishing, Ely, Cambridgeshire. ISBN (9781849285278) Ch 1, 2 & 3.
Woody, Aaron (2013). Enterprise security: A data-centric approach to securing the enterprise. Packt, Birmingham, UK. ISBN (9781849685962) Ch 1 & 2.
Soper, Daniel (2017). Information Privacy and Security. Security Lesson #1. Introduction to Computer Security https://www.youtube.com/watch?v=zBFB34YGK1U
Soper, Daniel (2017). Information Privacy and Security Security Lesson #2 Identification and Authentication.https://www.youtube.com/watch?v=pZIlaWhfhpQ&list=PLlYw7XsK0HV-r0T5fypBv9-a1gbq8xkZR&index=2
Rachana, Sok 3 5 Academic Context the McCumber Cube: https://www.youtube.com/watch?v=bwCae2V4kmY
Vlajic, N. InfoSecurity Presentation centered on CNSS Model, McCumber Cube for CNSS Security Model https://www.eecs.yorku.ca/course_archive/2013-14/F/4482/CSE4482_01_Introduction_2013_posted.pdf
Whitman, Michael and Mattord, Herbert (2010) Management of Information Security, 3rd Edition (ISBN-10: 1435488849) Ch 1.























Hello
YOU NEED QUALITY VISITORS FOR YOUR: sohail.life ?
WE PROVIDE HIGH-QUALITY VISITORS WITH:
– 100% safe for your site
– real visitors with unique IPs. No bots, proxies, or datacenters
– visitors from Search Engine (by keyword)
– visitors from Social Media Sites (referrals)
– visitors from any country you want (USA/UK/CA/EU…)
– very low bounce rate
– very long visit duration
– multiple pages visited
– tractable in google analytics
– custom URL tracking provided
– boost ranking in SERP, SEO, profit from CPM
CLAIM YOUR 24 HOURS FREE TEST HERE=> ventfara@mail.com
Thanks, Johnnie Merrett
Marys small rant made sense to me, Jerry you really should respect her opinion and then maybe the respect will be returned to you. We are all from different backgrounds and circumstances. http://www.xmc.pl
http://www.xmc.pl
Free links Thanks for the great article indeed…
http://www.pianino.xmc.pl
Youre so insightful, have so much real stuff to bring to the table. I hope that more people check out this and get what I got from it: chills. great job and great web publication. I cant wait to check out more, keep em comin!
http://www.pianino.xmc.pl
Smiac sie czesto i serdecznie, zdobyc szacunek ludzi inteligentnych i blyskotliwych a takze sympatie dzieci i mlodziezy – to znaczy odniesc prawdziwy realny sukces :-). R.W. Emerson. Do You Seen ? USA* Vortal > http://www.USA.XMC.PL
http://www.metale.xmc.pl
I am going to go ahead and bookmark this post for my sis for the research project for school. This is a pretty web page by the way. Where did you pick up the theme for this webpage?
http://www.socjologia.xmc.pl
Usefull points written on your blog, most I agree with. Recall viewing a similar blog which I will look to post. I will bookmark ofcourse I look forward your next thought provoking blog post http://www.xmc.pl
http://www.japan.m106.com
I was just chatting with my coworker about this today at lunch . Don’t remember how we got on the subject in fact, they brought it up. I do recall eating a wonderful steak salad with cranberries on it. I digress
http://www.xmc.pl
Jezeli ludzie szepcza i knuja za twoimi plecami to tylko znaczy ze ich wyprzedziles…
http://www.norwegia.xmc.pl